In today’s digital landscape, security is paramount, especially when it comes to cloud computing. As businesses increasingly rely on Amazon Web Services (AWS) for their infrastructure needs, securing the AWS platform becomes a critical priority. In this blog post, we will explore the concept of preventive measures in AWS security and how they play a crucial role in building a robust and secure platform.
Cloud Security on Amazon Web Services (Part I)
Building a Fortified Cloud: Exploring Preventive Measures for Secure AWS Platforms
Building a Secure AWS Platform: The Power of Preventive Measures
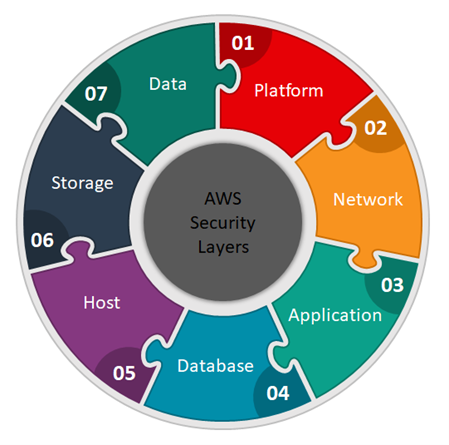
Assessment Layers
When conducting a security assessment, it’s important to consider multiple layers of security to ensure comprehensive protection of assets and systems. Here are the different layers typically involved in a security assessment, along with a brief explanation of each.
Platform Security
Ensuring the protection of the underlying cloud or hosting platform through robust security controls and measures.
Network Security
Implementing measures and controls to protect the organization’s network infrastructure from unauthorized access, threats, and vulnerabilities.
Application Security
Implementing safeguards and practices to protect software applications from potential threats, vulnerabilities, and unauthorized access.
Database Security
Implementing measures and controls to protect databases and ensure the confidentiality, integrity, and availability of data stored within them.
Host Security
Implementing measures and controls to protect individual hosts, including servers, workstations, and endpoints, from unauthorized access, malware, and other security threats.
Storage Security
Implementing measures and controls to ensure the protection, integrity, and confidentiality of data stored in storage systems, both in cloud and on-premises environments.
Data Security
Implementing measures and controls to protect sensitive data throughout its lifecycle, including data classification, encryption, access controls, and data loss prevention, to safeguard against unauthorized access, breaches, and data leakage.
DATA PROTECTION
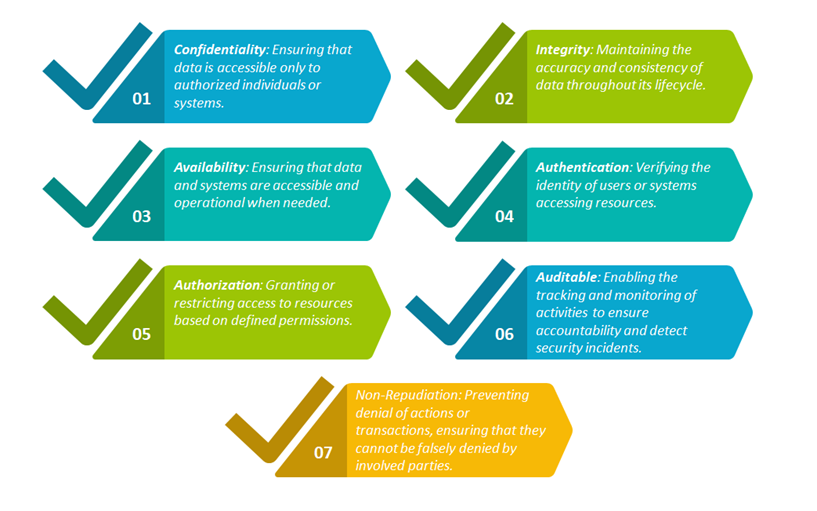
– Data protection aims to maintain the privacy and trustworthiness of data throughout its lifecycle, including storage, transmission, processing, and disposal.
-Safeguarding data to ensure confidentiality, integrity, and availability while enforcing authentication, authorization, auditable measures, and non-repudiation.
TYPES OF CONTROL
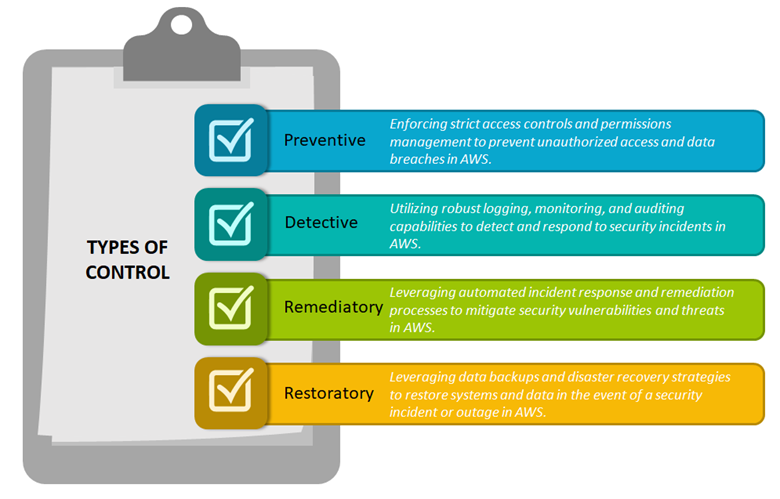
It is important to implement a combination of these control types to establish a comprehensive and layered security approach in AWS environments. Each control type plays a specific role in preventing, detecting, and responding to security threats, ensuring the overall security and protection of AWS resources and data.
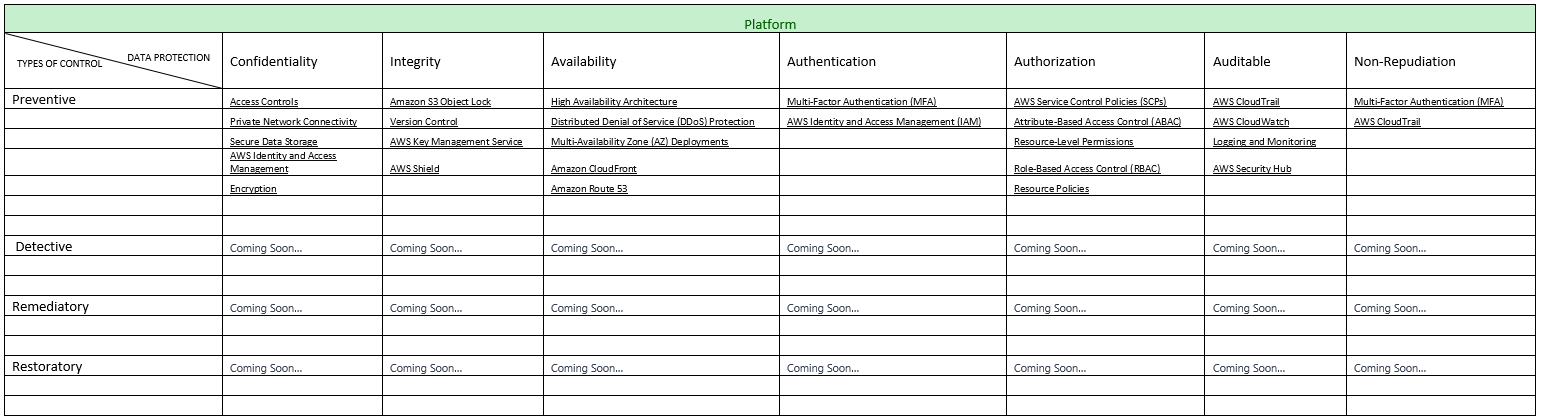
Preventive | Confidentiality
- Access Controls: AWS Identity and Access Management (IAM) allows you to manage user access and permissions to AWS resources, ensuring that only authorized individuals can access confidential data.
- Private Network Connectivity: AWS Virtual Private Cloud (VPC) enables you to create isolated networks and control access to resources within that network, adding an extra layer of confidentiality.
- Secure Data Storage: AWS provides services like Amazon S3 and Amazon EBS that offer robust security features like server-side encryption and access control mechanisms to protect confidential data.
- AWS Identity and Access Management (IAM): IAM allows you to manage user access to AWS services and resources. By defining granular permissions, you can ensure that only authorized individuals or processes can access confidential data or perform specific actions. IAM enables you to control access to AWS APIs, services, and management consoles.
- Encryption: AWS offers services like AWS Key Management Service (KMS) and AWS Certificate Manager (ACM) to encrypt data at rest and in transit, ensuring confidentiality.
Preventive | Integrity
- Amazon S3 Object Lock: Amazon S3 Object Lock feature allows you to enforce write-once-read-many (WORM) behavior for objects stored in Amazon S3. Once an object is locked, it cannot be modified or deleted for a specified retention period. This feature helps ensure the integrity and immutability of data stored in S3.
- AWS Key Management Service (KMS): AWS KMS plays a crucial role in ensuring data integrity by providing centralized key management. With AWS KMS, you can generate and control encryption keys used to protect data at rest and in transit. By managing access to encryption keys, you can prevent unauthorized modification or tampering of data.
- AWS Shield: AWS Shield is a managed Distributed Denial of Service (DDoS) protection service. It helps protect applications and data from volumetric, state-exhaustion, and other types of DDoS attacks that can potentially compromise data integrity. AWS Shield provides automated protections and leverages global threat intelligence to detect and mitigate DDoS attacks.
- Version Control: Utilize version control systems to track and manage changes to code and configurations, ensuring integrity throughout the development and deployment process. Using Version Control solutions on AWS allows development teams to deploy hybrid and cloud-native version control systems that can scale with game project size while also ensuring assets remain secure and available.
Preventive | Availability
- High Availability Architecture: Design and implement redundant systems, load balancers, and failover mechanisms to ensure continuous availability of applications and services.
- Distributed Denial of Service (DDoS) Protection: Utilize AWS Shield or other DDoS protection services to mitigate and prevent DDoS attacks that could disrupt availability.
- Multi-Availability Zone (AZ) Deployments: AWS provides the capability to deploy resources across multiple Availability Zones within a region. Availability Zones are physically separate data canters with independent power, cooling, and networking infrastructure. By distributing resources across multiple AZs, you can achieve high availability and protect against failures in a single zone.
- Amazon CloudFront: Amazon CloudFront is a content delivery network (CDN) service that helps improve availability and performance by caching content closer to end-users. It distributes content across multiple edge locations globally, reducing latency and improving the availability of web applications and static assets.
- Amazon Route 53: Route 53 is AWS’s scalable domain name system (DNS) web service. It offers features such as health checks and DNS failover to route traffic to healthy resources, helping to ensure the availability of your applications and services even in the event of infrastructure failures.
Preventive | Authentication
- Multi-Factor Authentication (MFA): Require users to authenticate using multiple factors, such as passwords and a second factor like SMS codes, authenticator apps, or hardware tokens.
- Identity and Access Management (IAM): Implement IAM policies and roles to control and manage user access to AWS resources.
Preventive | Authorization
- AWS Service Control Policies (SCPs): SCPs are used with AWS Organizations to set fine-grained permissions that apply to member accounts. SCPs allow you to control which AWS services and actions can be accessed within an organization, helping enforce authorization policies and restrictions across multiple accounts.
- Attribute-Based Access Control (ABAC): Implement ABAC policies that use attributes and conditions to determine access rights based on specific attributes of the requester.
- Resource-Level Permissions: With IAM, you can define permissions at a granular level, allowing you to control access to individual AWS resources. IAM policies can specify which actions are allowed or denied for specific resources, such as S3 buckets, EC2 instances, or RDS databases. This enables you to implement the principle of least privilege, granting users only the permissions they need to perform their tasks.
- Role-Based Access Control (RBAC): Define and enforce granular access controls based on roles and responsibilities to limit access to sensitive resources.
- Resource Policies: AWS services such as Amazon S3, Amazon SQS, and Amazon SNS support resource-based policies. These policies allow you to define permissions directly on the resources themselves. Resource policies provide an additional layer of authorization control, enabling you to specify access permissions for specific resources or resource hierarchies.
Preventive | Auditable
- AWS CloudTrail: AWS CloudTrail provides detailed logs of API calls and activities within your AWS account. It records important events such as user logins, API calls, resource modifications, and security-related events. CloudTrail logs are stored in Amazon S3 and can be used for security analysis, troubleshooting, and compliance purposes. CloudTrail also integrates with AWS CloudWatch for real-time monitoring and alerting based on specific events.
- AWS CloudWatch: AWS CloudWatch is a monitoring and logging service that collects and tracks metrics, logs, and events across your AWS resources and applications. CloudWatch provides a centralized dashboard for monitoring performance, generating alarms, and triggering notifications based on predefined thresholds. It allows you to gain visibility into your environment and facilitates auditing by capturing and analyzing logs and metrics.
- Logging and Monitoring: Enable AWS CloudTrail to log API calls and AWS Config to track configuration changes and utilize AWS CloudWatch for monitoring and alerting on specific events or metrics.
- AWS Security Hub: AWS Security Hub is a comprehensive security service that provides a centralized view of security findings and compliance status across multiple AWS accounts. It aggregates and prioritizes security alerts from various AWS services, third-party security tools, and AWS partner solutions. Security Hub helps you identify security risks, manage compliance, and track the resolution of security findings.
Preventive | Non-Repudiation
- Multi-Factor Authentication (MFA): AWS supports MFA, which adds an extra layer of security to user authentication. With MFA, users are required to provide a second form of authentication, such as a unique code generated by a virtual or physical MFA device, in addition to their username and password.
- AWS CloudTrail: AWS CloudTrail provides detailed logs of API calls and activities within your AWS account. These logs are designed to be tamper-proof and are digitally signed to prevent modification. By capturing and storing information about API actions and events, CloudTrail enables you to prove that specific actions were performed within your account, ensuring non-repudiation.
References:
KMS – https://aws.amazon.com/blogs/security/how-to-help-protect-sensitive-data-with-aws-kms/
ACM – https://aws.amazon.com/blogs/security/choosing-the-right-certificate-revocation-method-in-acm-private-ca/
IAM: https://aws.amazon.com/blogs/security/writing-iam-policies-how-to-grant-access-to-an-amazon-s3-bucket/
VPC: https://aws.amazon.com/blogs/security/securely-connect-to-linux-instances-running-in-a-private-amazon-vpc/
S3 : https://aws.amazon.com/blogs/security/how-to-use-bucket-policies-and-apply-defense-in-depth-to-help-secure-your-amazon-s3-data/
EBS: https://aws.amazon.com/blogs/security/how-to-create-a-custom-ami-with-encrypted-amazon-ebs-snapshots-and-share-it-with-other-accounts-and-regions/
MFA: https://aws.amazon.com/blogs/security/securing-access-to-aws-using-mfa-part-2/
AWS Config: https://aws.amazon.com/blogs/security/how-to-audit-your-aws-resources-for-security-compliance-by-using-custom-aws-config-rules/
IDS: https://aws.amazon.com/blogs/security/how-to-monitor-host-based-intrusion-detection-system-alerts-on-amazon-ec2-instances/
DLP: https://aws.amazon.com/blogs/architecture/bbva-architecture-for-large-scale-macie-implementation/
ELB: https://aws.amazon.com/blogs/security/exclude-cipher-suites-at-the-api-gateway-using-a-network-load-balancer-security-policy/
Auto Scaling: https://aws.amazon.com/blogs/compute/implementing-autoscaling-for-ec2-mac-instances/
Route 53: https://aws.amazon.com/blogs/security/how-to-automate-updates-for-your-domain-list-in-route-53-resolver-dns-firewall/
Written By: Umashankar N, Matheshsivatharshan S, and Preeth M
If you have any questions or suggestions, please reach out to us at contactus@1cloudhub.com
