Based on the scenario above, each time we need to log in to the instance and list the patches in the inventory and select the patches that we need to install in the instances.
It would take more time and a manual process to be completed. This may cause a risk factor of missing patches in some of the instances, creating vulnerability issues and we may end up opening the 22 ports for all instances to access the machines and install the patches.
Solution
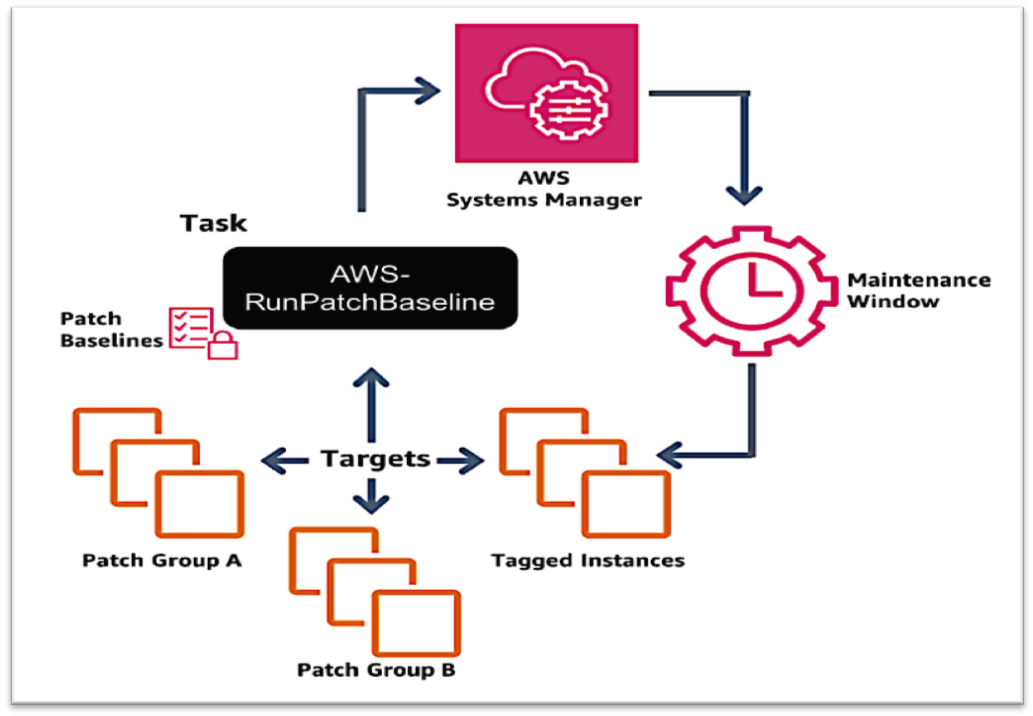
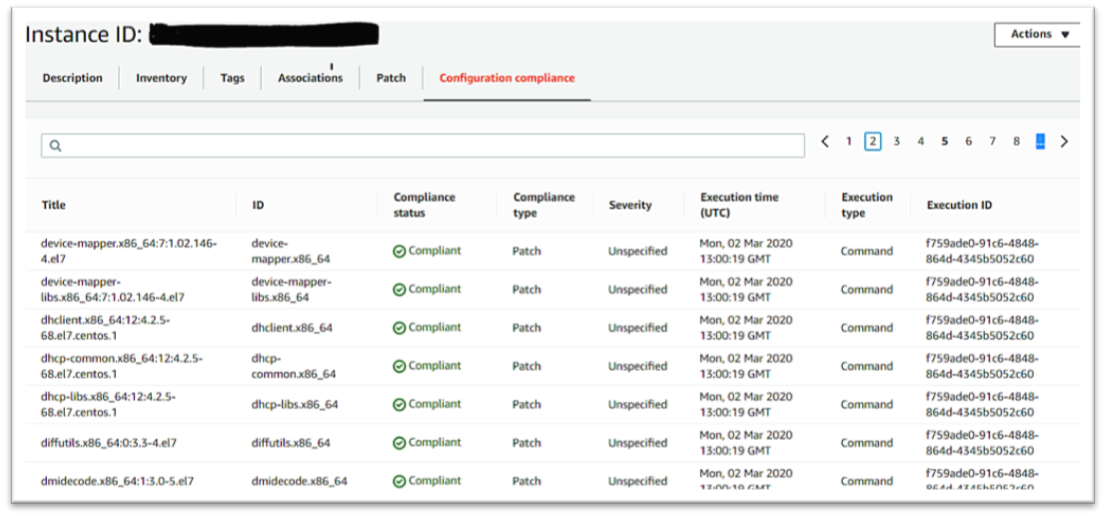
AWS System Manager (SSM) is the perfect solution for the above scenario. System manager is a service that enables you to automation without logging into the system. SSM can automate the task, collecting the system inventory, applying OS patches and execute the scripts without logging the instances (Linux / Windows) using SSM.
Usually, admin maintains a bastion instance by logging in to other servers, and Admin manages SSH keys and passwords to log in to other instances. But using SSM, we don’t need bastion instances to log in to other servers (Bastion-free environment), it gives additional security to all instances. There’s no need to open ports.
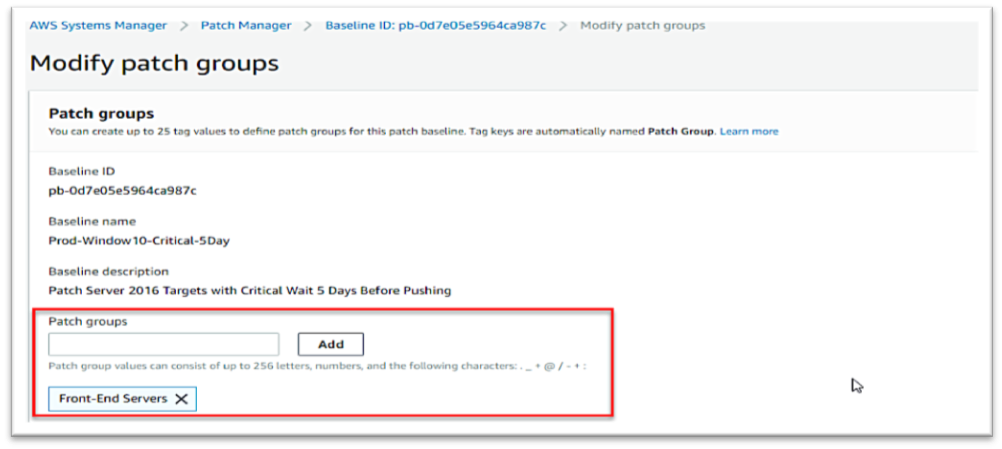
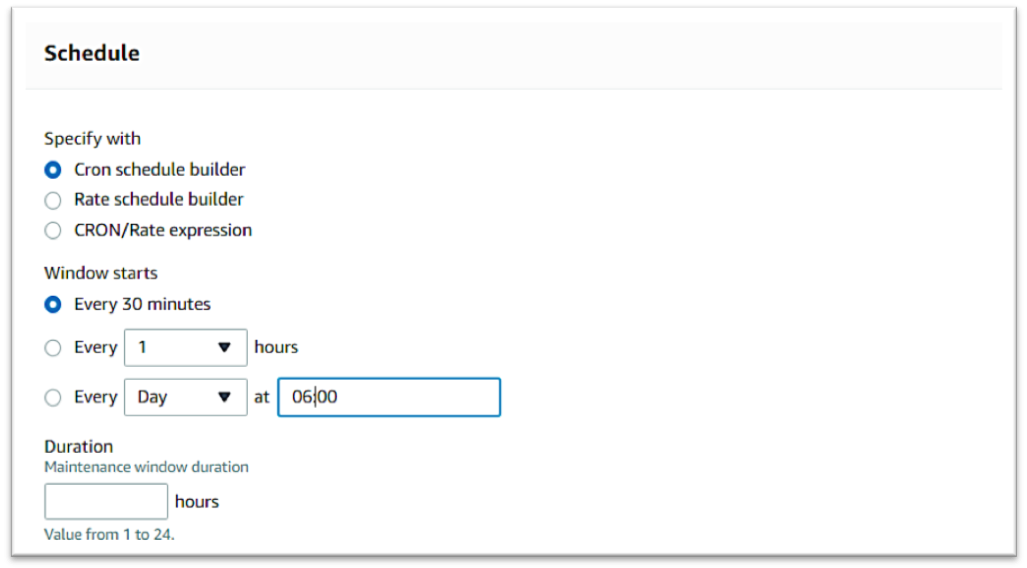
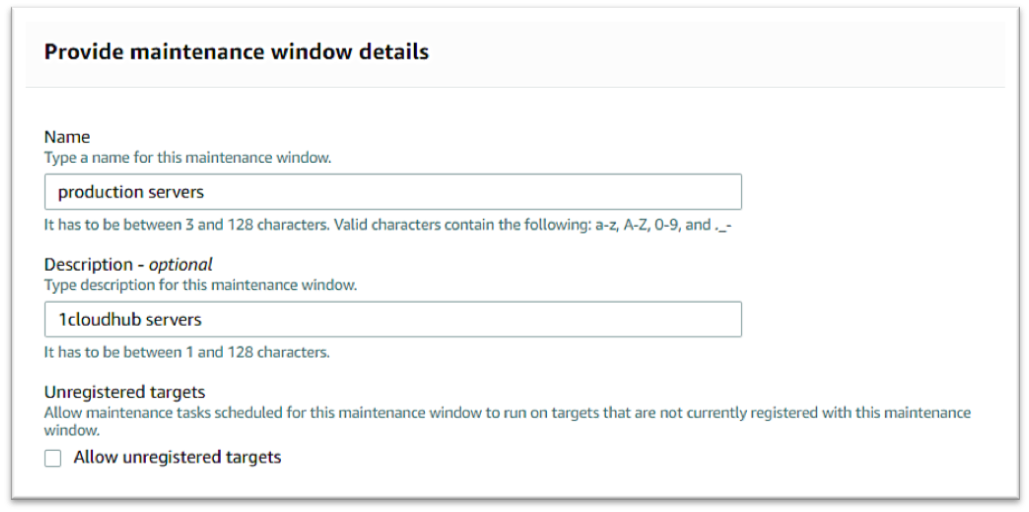
AWS System Manager
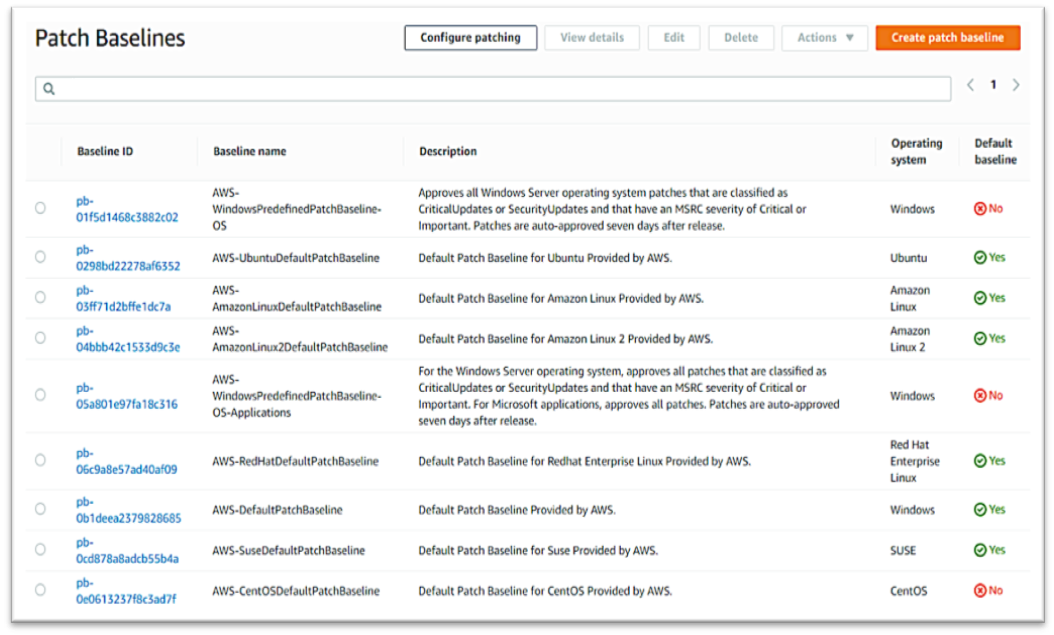
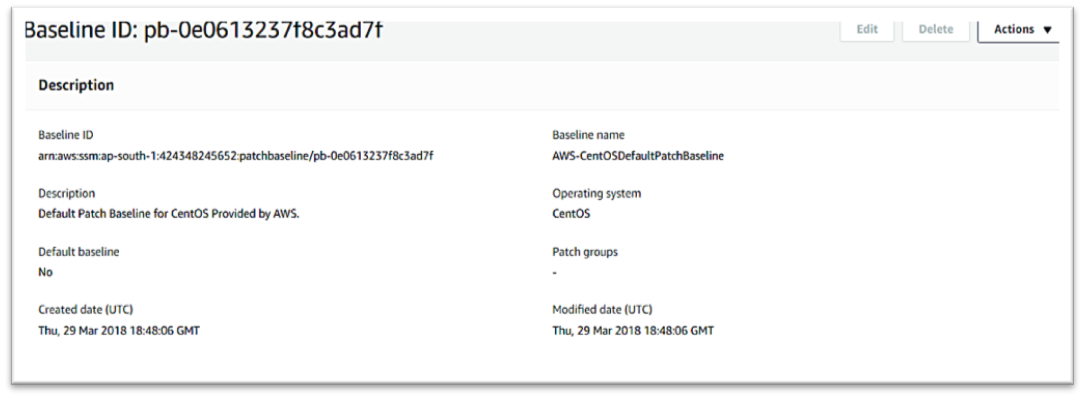
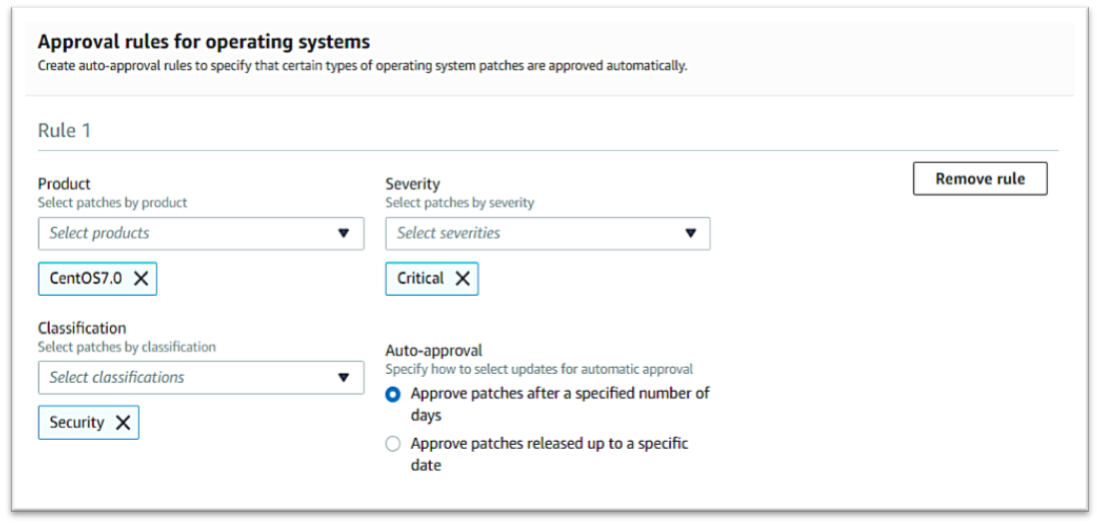
Amazon EC2 Systems Manager lets you automatically apply OS patches to customized maintenance windows, collect software inventory, and configure Windows and Linux operating systems. One of the features of System Manager is the Patch Manager, which can automate the patching process for Windows managed instances on a scale. With Patch Manager, you can scan instances for missing patches or search and install missing patches to individual instances or large groups of instances using EC2 tags. Patch Manager can also be used for Windows Systems Manager Maintenance, and you can create a schedule within a customized maintenance window to conduct patch operations on your instances.