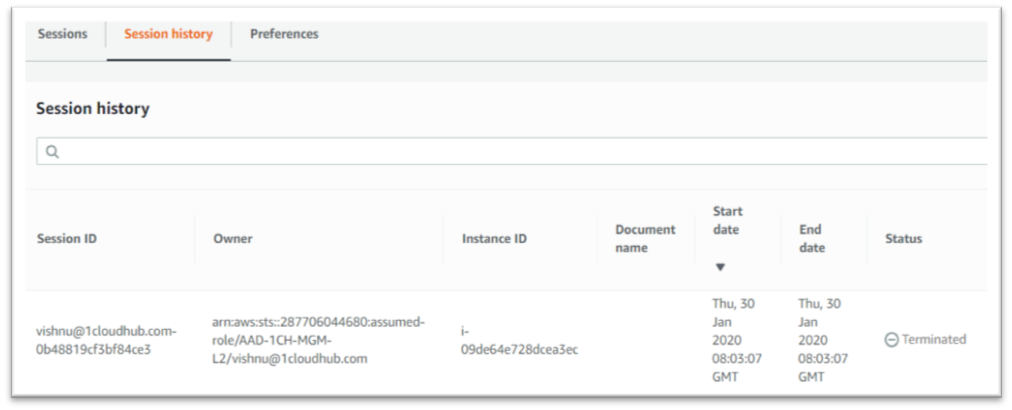
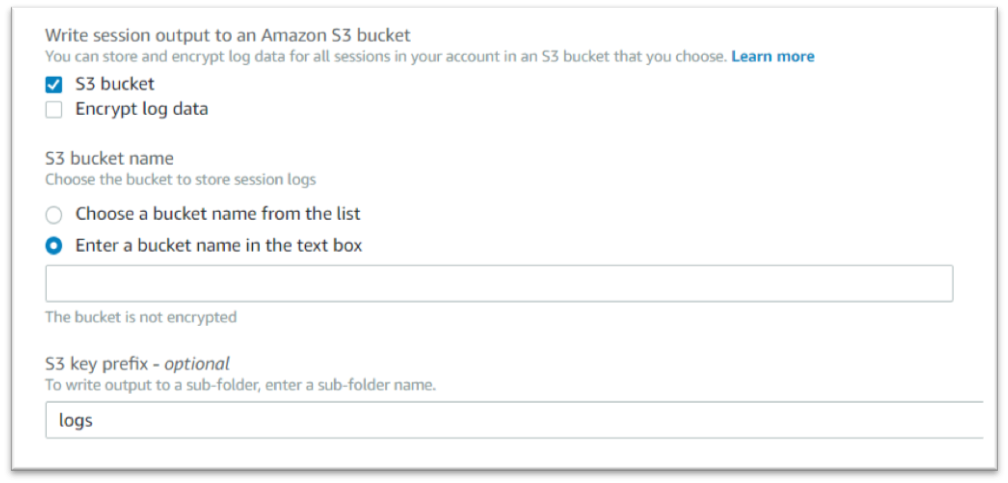
Session Manager is fully managed by the AWS system manager that can be used to manage the EC2 instance and allow users to connect to the instances without using RDP or SSH. It provides secure instance management without opening inbound ports or setting up bastion hosts or managing the SSH keys.
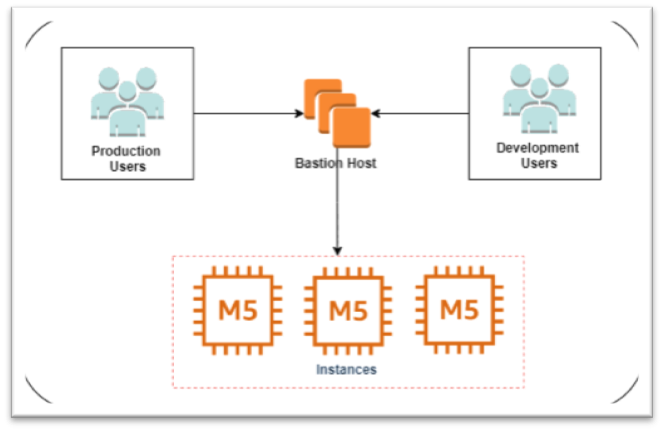
It is well known that one are not able to directly access EC2 instances unless there is VPN Connectivity or Direct Connect or other network connectivity source with the VPC. Alternatively, connecting to VPC requires an intermediate instance, such as a bastion host or a jump box, which is hosted on a public subnet and connects private subnet instances. Using SSM Session Manager, one can connect to private instances directly without using bastion hosts or opening any ports in security groups or whitelisting ports in the CIDR. Session Manager adds the additional layer of security to the EC2 instances.